Global User Management
Comprehensive guide to managing global users and platform-level permissions in Tacnode's Context Lake environment.
Global user management in Tacnode provides centralized control over platform-level access and permissions across your entire Context Lake environment. This system enables administrators to manage user access to Context Lake instances, databases, and platform services from a single interface.
Understanding Context Lake Roles
Tacnode uses a hierarchical role system for Context Lake management, providing different levels of access and capabilities based on organizational needs.
Built-in Context Lake Roles
| Role | Full Name | Capabilities | Use Cases |
|---|---|---|---|
| admin | admin@{id}.contextlakes | Full platform administration | CTO, Data Engineering Leaders |
| devops | devops@{id}.contextlakes | Infrastructure management | DevOps Engineers, Platform Teams |
| viewer | viewer@{id}.contextlakes | Read-only platform access | Analysts, Reporting Users |
Role Capabilities Matrix
Admin Role (admin@{id}.contextlakes)
- Complete Context Lake instance lifecycle management
- User and role management across the platform
- Access to all databases and nodegroups
- Platform configuration and settings management
- Billing and subscription management
DevOps Role (devops@{id}.contextlakes)
- Context Lake instance operations and monitoring
- Nodegroup creation, scaling, and management
- Database deployment and configuration
- Performance monitoring and troubleshooting
- Infrastructure automation and scripting
Viewer Role (viewer@{id}.contextlakes)
- Read-only access to all Context Lake resources
- Query execution on all accessible databases
- Monitoring dashboard and metrics viewing
- Report generation and data export
- Documentation and schema browsing
Role Hierarchy and Inheritance
Context Lake Role Structure
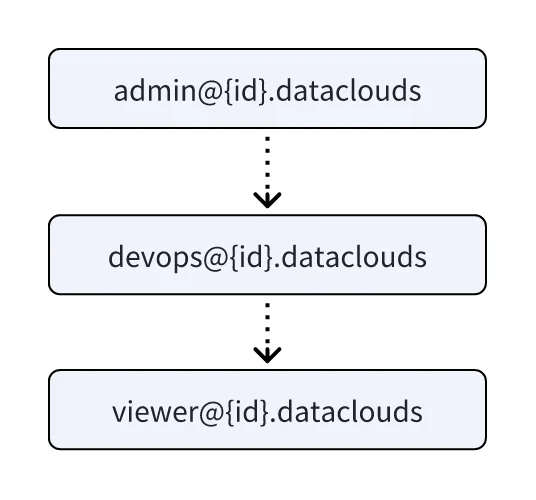
The role hierarchy follows this structure:
- Admin: Top-level role with complete platform control
- DevOps: Operations-focused role with infrastructure management
- Viewer: Read-only role for data consumption and monitoring
Inheritance Rules:
- Admin role includes all DevOps and Viewer capabilities
- DevOps role includes all Viewer capabilities
- Viewer role provides baseline access for data consumption
Managing Context Lake Permissions
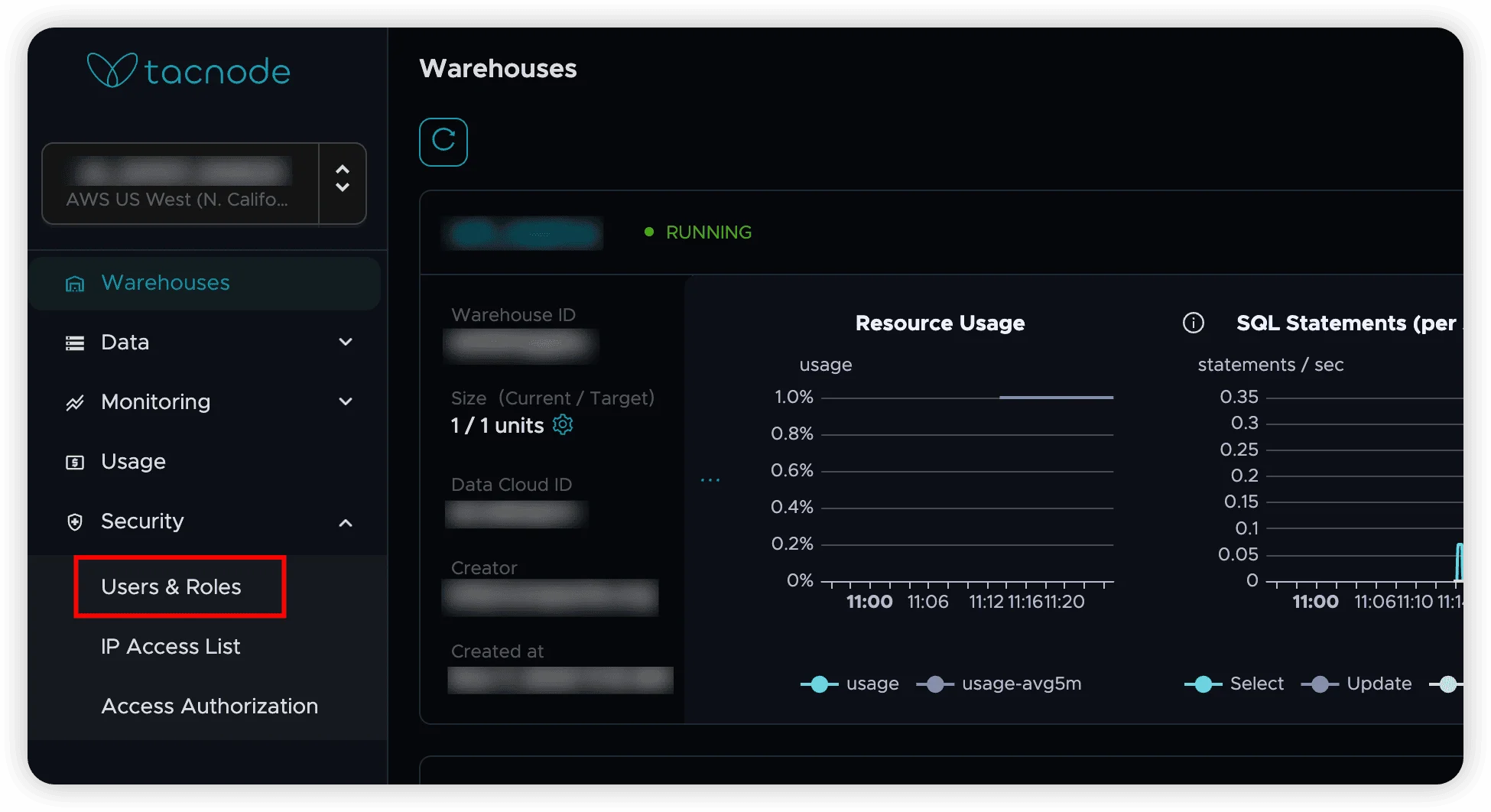
Accessing Permission Management
-
Navigate to Context Lake Settings
- Log into the Tacnode platform
- Select Context Lakes from the main navigation
- Choose your specific Context Lake ID
- Click Permission Management
-
View Current Permissions
- Review existing role assignments
- Understand current user access levels
- Identify permission gaps or overlaps
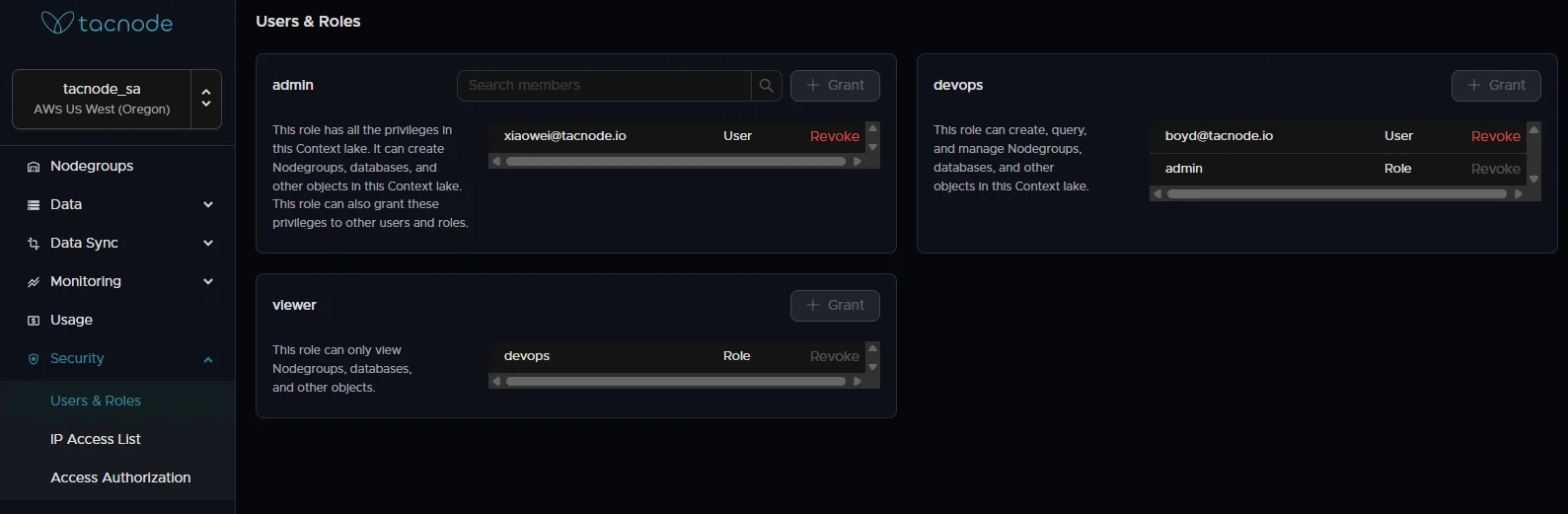
Adding Users to Context Lake Roles
Step-by-Step Process:
-
Select Target Role
- Click Authorize User next to the appropriate role
- Choose between admin, devops, or viewer based on user needs
-
Specify User Email
- Enter the email address of the intended user
- Ensure the email is registered with the Tacnode platform
- Verify the user’s identity and authorization level
-
Confirm Assignment
- Review the role assignment details
- Click OK to complete the assignment
- User will receive notification of their new access
Database Access Authorization
After assigning Context Lake roles, users need database-level access to connect and query data.
Prerequisites for Database Access
- User must have a registered Tacnode platform account
- User must be assigned to at least one Context Lake role
- Database must be accessible within the Context Lake
Granting Database Login Permissions
Using Administrator Account:
-
Connect as Database Administrator
-- Connect using psql or preferred database client psql -h your-nodegroup.tacnode.io -U admin -d your_database -
Create Global User Account
-- For regular users CREATE USER "user@example.com"; -- For users requiring administrative privileges CREATE USER "admin@example.com" WITH SUPERUSER;
Important: Only email addresses registered on the Tacnode platform are supported. Attempting to create users with unregistered emails will result in an error: ERROR: a role/user named auth@example.com has not been registered yet.
Superuser Caution: Granting superuser privileges provides unrestricted database access. Use this privilege sparingly and only for trusted administrators.
Best Practice: Fine-Grained Authorization
Instead of granting broad permissions, implement role-based access control with specific database roles:
-- Create business-specific schemas
CREATE SCHEMA erp;
CREATE SCHEMA bi;
-- Create functional roles
CREATE ROLE bi_full_access;
CREATE ROLE erp_read_only;
-- Grant schema-level permissions
GRANT ALL ON ALL TABLES IN SCHEMA bi TO bi_full_access;
GRANT USAGE, CREATE ON SCHEMA bi TO bi_full_access;
GRANT SELECT ON ALL TABLES IN SCHEMA erp TO erp_read_only;
GRANT USAGE ON SCHEMA erp TO erp_read_only;
-- Assign roles to users
CREATE USER "analyst@example.com";
GRANT bi_full_access TO "analyst@example.com";
GRANT erp_read_only TO "analyst@example.com";Removing Users from Context Lake Roles
Removal Process:
-
Navigate to Permission Management
- Access the Context Lake permission interface
- Locate the user to be removed
-
Initiate Removal
- Click the red × icon next to the user’s name
- Review the removal confirmation details
-
Confirm Removal
- Click OK in the confirmation dialog
- User access will be immediately revoked
Security Best Practices
User Account Management
- Regular Access Reviews: Conduct quarterly reviews of user access and permissions
- Principle of Least Privilege: Grant minimum necessary permissions for each user
- Account Lifecycle: Implement processes for onboarding and offboarding users
- Strong Authentication: Ensure all users have strong passwords and MFA enabled
Role Assignment Guidelines
- Admin Role: Limit to 2-3 trusted individuals maximum
- DevOps Role: Assign to platform engineers and infrastructure teams
- Viewer Role: Default assignment for data consumers and analysts
- Regular Auditing: Track and audit all role assignments and changes
Database Access Controls
- Schema-Based Separation: Use database schemas to logically separate different business domains
- Role-Based Permissions: Create functional roles instead of granting direct permissions to users
- Connection Monitoring: Monitor database connections and query patterns
- Access Logging: Enable audit logging for all database access and operations
Troubleshooting Common Issues
User Registration Errors
Error: ERROR: a role/user named auth@example.com has not been registered yet
Solution:
- Verify the user has registered an account on the Tacnode platform
- Check email address spelling and format
- Ensure the user has completed email verification
Permission Inheritance Issues
Problem: User has Context Lake role but cannot access databases
Solution:
- Verify database-level permissions have been granted
- Check that the user’s global account has been created in the target database
- Confirm the user is connecting to the correct nodegroup and database
Role Assignment Failures
Problem: Cannot assign roles to certain users
Solution:
- Ensure you have admin privileges for the Context Lake
- Verify the target user’s email is correctly registered
- Check for any platform-level restrictions or quotas
Frequently Asked Questions
Q: Can I create custom Context Lake roles? A: Currently, Tacnode supports only the three built-in roles (admin, devops, viewer). Custom role creation is not available.
Q: Can I modify the inheritance relationships between roles? A: The inheritance relationships for system roles cannot be modified. However, you can change role assignments for individual users.
Q: How do I identify which roles a user has inherited? A: In the permission management interface, users show their direct role assignments. Inherited permissions are indicated in the role hierarchy display.
Q: What happens when a Context Lake is deleted? A: All role assignments and permissions associated with the Context Lake are automatically removed. Users lose access to all resources within that Context Lake.
This comprehensive global user management system ensures secure, scalable access control across your entire Tacnode platform while maintaining operational flexibility and security best practices.