Cloud Native
Discover how to leverage cloud-native technology with Tacnode. Get started with our comprehensive guide to building scalable, resilient applications in the cloud.
Tacnode offers cloud-agnostic, fully managed data services through innovative cloud-native technologies.
Cloud-Agnostic Architecture
Tacnode’s computing abstraction is the Nodegroup, which provides computing services to users. Users can connect directly to the Nodegroup using a PostgreSQL-compatible client or methods like JDBC/ODBC. A Nodegroup comprises multiple computing units (Units), managed using K8S container technology for easy and rapid horizontal scaling to enhance computing power. Charges are based on the number of computing units used and the duration.
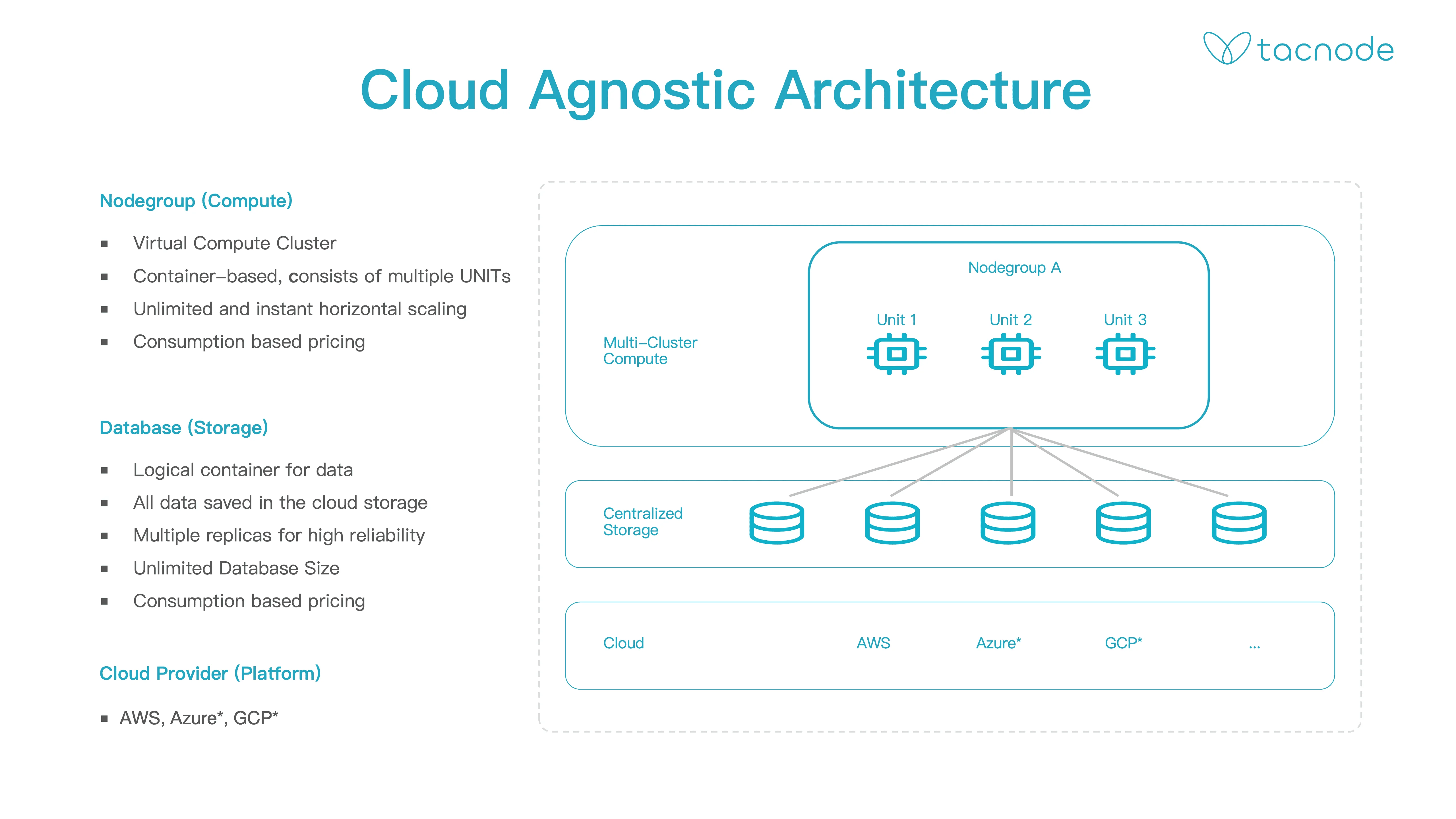
Tacnode’s storage abstraction is a database. Users combine business-related data to form a database, a logical storage unit. Data is physically stored in cloud storage, such as block storage (EBS, etc.) and object storage (S3, OSS, etc.). The data volume in a single Tacnode database is unlimited, with storage and computing billed per use.
Tacnode utilizes standard cloud components like EBS and S3 and containerization technology like K8S, enabling quick service deployment across major cloud providers.
Fully-managed
Public clouds offer elasticity, but resource allocation often takes minutes, which doesn’t meet Tacnode’s need for second-level scaling. Tacnode addresses this with a fully managed service on the public cloud and a shareable resource pool, enabling rapid scaling at lower costs. In case of public cloud machine failures, the fully managed service uses the resource pool for automatic failover, ensuring High-Availability.
Tacnode’s fully managed service includes monitoring capabilities, providing insights into Nodegroup operations, database sizes, and more.
The service also offers automatic backup capabilities, allowing users to restore data to a correct backup if incorrect data is written.
Tacnode provides Open APIs, enabling users to automate management operations through scripts, implementing infrastructure as code with a cloud-native development model.
Security & Compliance
Data security is Tacnode’s top priority. To ensure system safety and reliability, Tacnode continuously invests in security, enhancing it in several ways.
Private Link: Recommended for all users to connect to Tacnode, ensuring only applications and clients in the user’s VPC can access the system, preventing unauthorized network access.
IP Access List: When Private Link isn’t feasible and the public network is used, Tacnode supports a public network access list. Users can add client IPs to the list, ensuring connections only from listed machines, effectively preventing malicious attacks.
Fine-grained access control: Supports detailed access control for legitimate users, with row-level and column-level permission control for precise data access management.
Data encryption: Tacnode encrypts stored data, ensuring that hackers, cloud vendors, or service providers cannot access specific data content, enhancing data security.